14.3. rc.DMZ.firewall.txt
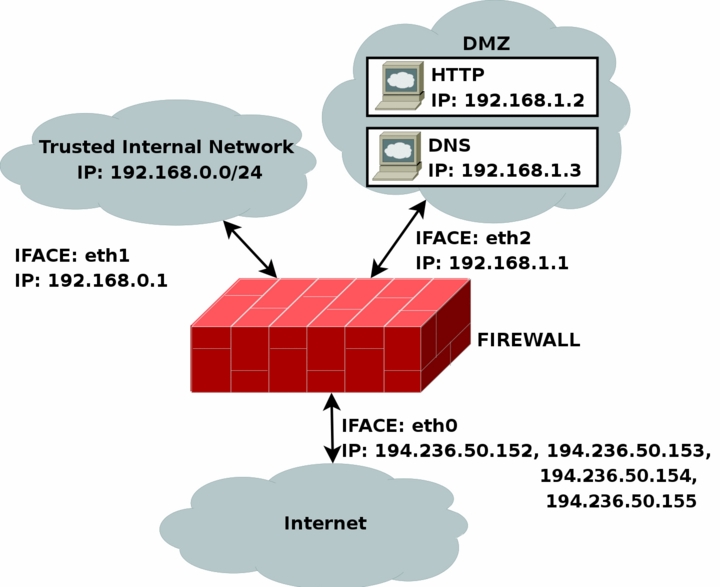
The rc.DMZ.firewall.txt script was written for those people out there that have one Trusted Internal Network, one De-Militarized Zone and one Internet Connection. The De-Militarized Zone is in this case 1-to-1 NATed and requires you to do some IP aliasing on your firewall, i.e., you must make the box recognize packets for more than one IP. There are several ways to get this to work, one is to set 1-to-1 NAT, another one if you have a whole subnet is to create a subnetwork, giving the firewall one IP both internally and externally. You could then set the IP's to the DMZed boxes as you wish. Do note that this will "steal" two IP's for you, one for the broadcast address and one for the network address. This is pretty much up to you to decide and to implement. This tutorial will give you the tools to actually accomplish the firewalling and NATing part, but it will not tell you exactly what you need to do since it is out of the scope of the tutorial.
The rc.DMZ.firewall.txt script requires these options to be compiled into your kernel, either statically or as modules. Without these options, at the very least, available in your kernel, you will not be able to use this scripts functionality. You may in other words get a lot of errors complaining about modules and targets/jumps or matches missing. If you are planning to do traffic control or any other things like that, you should see to it that you have all the required options compiled into your kernel there as well.
CONFIG_NETFILTER
CONFIG_IP_NF_CONNTRACK
CONFIG_IP_NF_IPTABLES
CONFIG_IP_NF_MATCH_LIMIT
CONFIG_IP_NF_MATCH_STATE
CONFIG_IP_NF_FILTER
CONFIG_IP_NF_NAT
CONFIG_IP_NF_TARGET_LOG
You need to have two internal networks with this script as you can see from the
picture. One uses IP range 192.168.0.0/24 and consists of a Trusted
Internal Network. The other one uses IP range 192.168.1.0/24 and
consists of the De-Militarized Zone which we will do
1-to-1 NAT to. For example, if someone from the
Internet sends a packet to our DNS_IP, then we use
DNAT to send the packet on to our
DNS on the DMZ network. When
the DNS sees our packet, the packet will be destined
for the actual DNS internal network IP, and not to our
external DNS IP. If the packet would not have been
translated, the DNS wouldn't have answered the packet.
We will show a short example of how the DNAT code
looks:
$IPTABLES -t nat -A PREROUTING -p TCP -i $INET_IFACE -d $DNS_IP \
--dport 53 -j DNAT --to-destination $DMZ_DNS_IP
First of all, DNAT can only be performed in the
PREROUTING chain of the nat
table. Then we look for TCP protocol on our
$INET_IFACE with destination IP that matches our
$DNS_IP, and is directed to port 53, which is the
TCP port for zone transfers between name servers. If
we actually get such a packet we give a target of
DNAT. After that we specify where we want the packet
to go with the --to-destination option and give it the value
of $DMZ_DNS_IP, in other words the IP of the
DNS on our DMZ network. This
is how basic DNAT works. When the reply to the
DNATed packet is sent through the firewall, it
automatically gets un-DNATed.
By now you should have enough understanding of how everything works to be able to understand this script pretty well without any huge complications. If there is something you don't understand that hasn't been gone through in the rest of the tutorial, mail me since it is probably a fault on my side.